LLDP is a layer 2 neighbor discovery protocol that allows devices to advertise device information to their directly connected peers/neighbors. It is best practice to enable LLDP globally to standardize network topology across all devices devices if you have a multi-vendor network. LLDP is an industry standard, vendor -neutral protocol. LLDP is disabled by default. To enable LLDP on the device, use `lldp run` on the global configuration mode. LLDP and CDP (CISCO DISCOVERY PROTOCOL) are similar protocols, CDP is a proprietary Data Link Layer protocol developed by Cisco Systems. It is used to share information about other directly connected Cisco equipment, such as the operating system version and IP address. The big difference between LLDP and CDP is that, LLDP is a standard while CDP is a Cisco proprietary protocol. Cisco devices Support IEE 802.1ab version of LLDP. This allows non Cisco devices to advertise information about themselves to our network devices.
CISCO DNA. What is Cisco DNA used for?
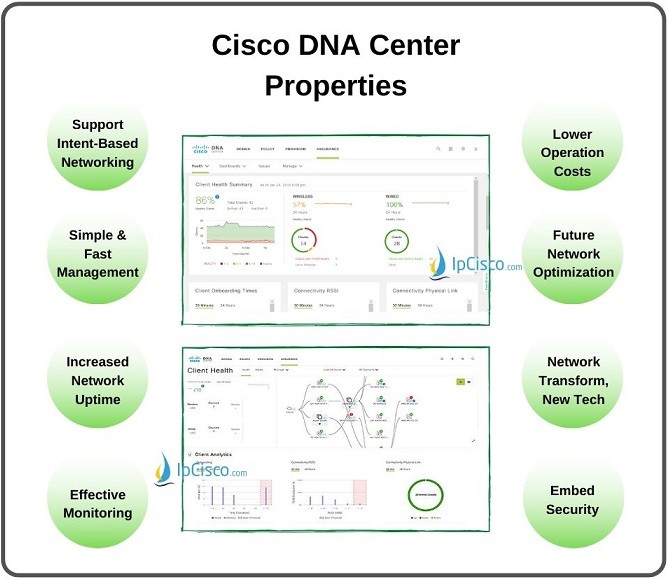
Cisco DNA Center is a complete software-based network automation and assurance solution. It's the dashboard for control and management of our intent-based. Cisco DNA provides a complete intent-based networking system that is constantly learning, adapting, and using contextual insights to make sure the network continuously responds to dynamic IT and business needs. Cisco DNA is the open, software-driven architecture that turns vision into reality.Cisco DNA Center is a powerful network controller and management dashboard that lets you take charge of your network, optimize your Cisco investment, find and resolve network issues with Cisco DNA Center. Cisco DNA Provides software-based network automation and assurance, Cisco DNA also Controls and manage intent-based networks.
Point-to-Point Protocol over Ethernet (PPPOE)
PPPOE is a network protocol that fascilitates communication between network endpoints. PPPoE is the point-to-point protocol running over the Ethernet at the link laye. It provides PPPoE connections on the Ethernet, sets up PPP sessions, and encapsulates PPPOE frames. PPPOE connect users to remote access devices, providing cost effective user access and excellent user access control. PPPOE suppports remote access to multiple user host over an ethernet and provides accounting data for transmission to ressolve application issues. PPPOE is therefore widely used for career network access.
Secure Shell
What is SSH used for?
SSH or Secure Shell is a network communication protocol that enables two computers to communicate (http or hypertext transfer protocol, which is the protocol used to transfer hypertext such as web pages) and share data. SSH protocol uses public key cryptography to authenticate the server, meaning the server sends its public key to the client for confirmation. The client is able to authenticate the server by comparing this host key against a local database or by receiving the verification of a Certified Authority. SSH is an important, useful and secured protocol, understanding how it works and how to SSH configuration is done is very essential.
SSH Configuration
The ssh configuration command provides a secure encrypted connection between two hosts over an insecure network. This connection can also be used for terminal access, file transfers, and for tunneling other application, before SSH Configuration is done, SSH commands need to be enabled. SSH Configuration in different in the various operating systems that exist. SSH Configuration file allows you to define specific settings for each SSH host that makes connecting to that host far easier. The SSH configuration file is also read by other programs such as scp, sftp, and rsync .




Comments