In today's digital era, where businesses rely heavily on technology to operate efficiently, ensuring the security of sensitive data and systems is paramount. With the increasing frequency and sophistication of cyber threats, organizations must adopt robust measures to safeguard their assets. One such measure that plays a crucial role in bolstering security is User Access Reviews (UAR). In this article, we delve into the significance of UAR, its benefits, and best practices for implementation.
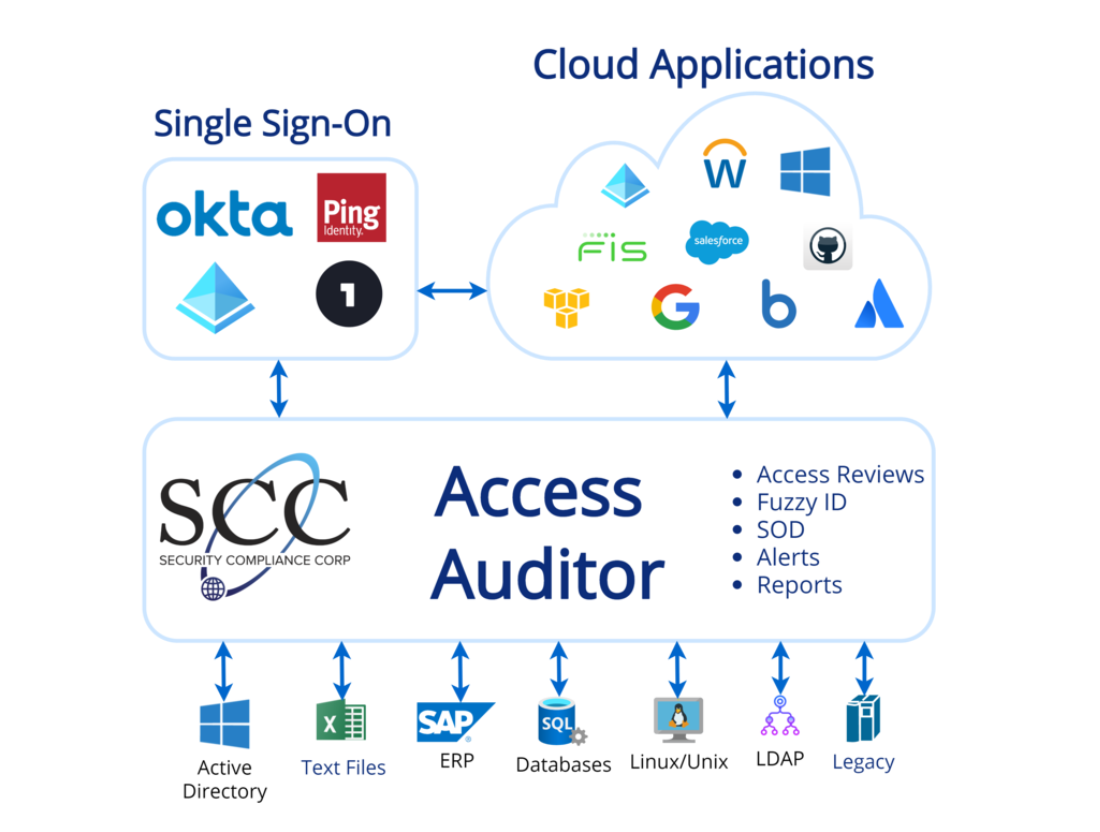
User Access Reviews, often referred to as access recertification or entitlement reviews, are systematic evaluations of user permissions and privileges within an organization's IT infrastructure. These reviews aim to verify that individuals have appropriate access rights aligned with their roles and responsibilities. By regularly assessing and validating user access, organizations can mitigate the risk of unauthorized access, data breaches, and insider threats.
The importance of conducting User Access Reviews cannot be overstated. Firstly, they help maintain compliance with regulatory requirements such as GDPR, HIPAA, PCI DSS, and others. Compliance standards mandate organizations to implement adequate controls to protect sensitive information and ensure that access to such data is restricted to authorized personnel only. Failure to comply with these regulations can result in severe penalties and reputational damage.
Secondly, User Access Reviews promote the principle of least privilege, which stipulates that users should be granted only the minimum level of access required to perform their job functions. Over time, users may accumulate unnecessary permissions due to role changes, job rotations, or neglectful administration. Conducting regular access reviews enables organizations to identify and rectify excessive privileges, reducing the attack surface and enhancing overall security posture.
Moreover, User Access Reviews play a vital role in detecting and preventing insider threats. Malicious insiders, whether intentionally or inadvertently, pose a significant risk to organizational security. By scrutinizing user access patterns and identifying anomalies, such as unauthorized access attempts or suspicious activity, organizations can proactively mitigate insider threats before they escalate into full-blown security incidents.
Implementing effective User Access Reviews requires adherence to best practices and leveraging appropriate tools and technologies. Here are some key steps to streamline the UAR process:
- Define Access Policies and Procedures: Establish clear guidelines for granting, modifying, and revoking user access rights. Document access policies and procedures to ensure consistency and accountability across the organization.
- Identify Stakeholders: Involve key stakeholders from IT, security, compliance, and business units in the UAR process. Define roles and responsibilities to facilitate collaboration and accountability.
- Automate Access Reviews: Leverage automated tools and identity management solutions to streamline the access review process. Automation helps reduce manual effort, ensure accuracy, and enable timely reviews.
- Schedule Regular Reviews: Set predefined intervals for conducting access reviews based on risk assessments, regulatory requirements, and organizational policies. Regular reviews help keep access privileges aligned with business needs and regulatory mandates.
- Perform Comprehensive Reviews: Evaluate user access rights across all systems, applications, and data repositories within the organization. Consider both user and system-generated entitlements to ensure a thorough assessment.
- Implement Segregation of Duties (SoD) Controls: Identify and mitigate conflicts of interest by enforcing SoD controls. Prevent individuals from having conflicting roles or permissions that could lead to fraudulent activities or data breaches.
- Enforce Recertification: Require users and their managers to recertify access rights periodically. This process ensures that access privileges remain appropriate and valid over time, especially in dynamic environments.
- Monitor and Audit Access Activity: Implement robust monitoring and auditing mechanisms to track user access activity, detect anomalies, and investigate suspicious behavior. Continuous monitoring helps identify security incidents in real-time and facilitates timely response and remediation.
In conclusion, User Access Reviews are essential for maintaining the integrity, confidentiality, and availability of organizational data and systems. By regularly reviewing and validating user access rights, organizations can mitigate the risk of data breaches, comply with regulatory requirements, and safeguard against insider threats. By following best practices and leveraging automation tools, businesses can streamline the UAR process and enhance overall security posture in today's evolving threat landscape.




Comments