Introduction
In today’s digital landscape, securing user access and managing identities effectively is critical for organizations of all sizes. With the increasing threat of cyberattacks, insider threats, and compliance requirements, businesses must adopt robust User Access Management and Identity Governance and Administration (IGA) solutions to ensure data security, reduce risks, and maintain compliance.
This article explores User Access Reviews, User Access Management, Identity Governance and Administration Solutions, and their significance in ensuring robust security and compliance frameworks.
Understanding User Access Reviews
User Access Reviews (UARs) are an essential component of access control strategies in an organization. These reviews help organizations regularly audit and validate the access rights of users to ensure they have the appropriate permissions.
Importance of User Access Reviews
- Security Enhancement: Regular user access reviews help identify and eliminate excessive or outdated privileges that can lead to security vulnerabilities.
- Regulatory Compliance: Industries like finance, healthcare, and government require compliance with frameworks such as GDPR, HIPAA, SOX, and ISO 27001. User access reviews ensure that organizations meet these standards.
- Reduction of Insider Threats: Employees with unnecessary access can pose security risks. Regular reviews mitigate this risk by enforcing the principle of least privilege (PoLP).
- Operational Efficiency: By maintaining proper access levels, organizations can streamline workflow processes and reduce inefficiencies.
Best Practices for Conducting User Access Reviews
- Automate the Review Process: Using an identity governance solution can significantly reduce manual effort and improve accuracy.
- Define Access Control Policies: Establish clear guidelines for granting, modifying, and revoking access.
- Segment Users by Role: Implement Role-Based Access Control (RBAC) to streamline the review process.
- Monitor and Audit Access Logs: Regular audits help detect anomalies and unauthorized access attempts.
- Engage Business Units: Involve department heads and stakeholders in the review process to ensure accuracy.
User Access Management: A Core Component of Identity Governance
User Access Management (UAM) focuses on managing user identities, credentials, and access permissions across an organization’s IT infrastructure.
Key Aspects of User Access Management
- User Provisioning & De-provisioning: Ensures that new employees, contractors, or partners receive the right level of access when they join and that their access is revoked when they leave.
- Access Control Mechanisms: Implementing strong authentication and authorization methods to prevent unauthorized access.
- Single Sign-On (SSO) and Multi-Factor Authentication (MFA): Enhances security and user experience.
- Access Monitoring & Reporting: Continuous monitoring of user activities and access levels to detect suspicious behaviors.
- Identity Lifecycle Management: Ensures that user accounts are managed efficiently throughout their tenure in an organization.
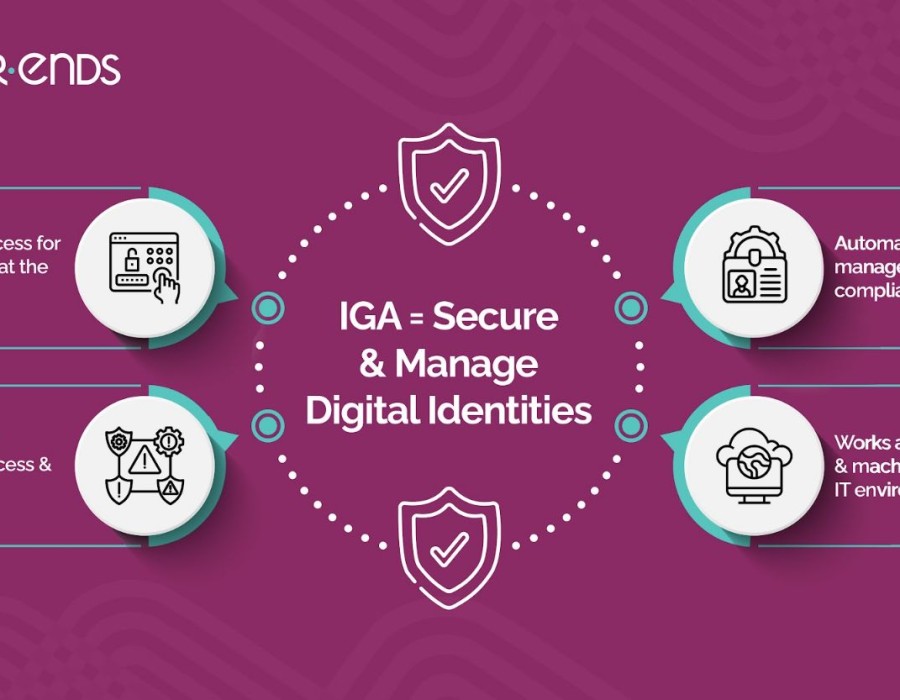
Identity Governance and Administration (IGA) Solution
An Identity Governance and Administration (IGA) solution provides organizations with tools to automate identity management, streamline user access, and enforce security policies effectively.
Features of an Effective Identity Governance and Administration Solution
- Automated User Access Reviews: Enables organizations to schedule and conduct regular access audits.
- Policy-Based Access Management: Ensures compliance with industry regulations through predefined policies.
- Integration with IT Systems: Connects with Active Directory, HR systems, and other applications for seamless identity management.
- Role-Based and Attribute-Based Access Control (RBAC & ABAC): Provides structured and policy-driven access control.
- AI and Machine Learning Capabilities: Enhances decision-making through predictive analytics and anomaly detection.
- Self-Service Access Requests: Empowers employees to request access with automated approval workflows.
Benefits of Implementing an Identity Governance and Administration Solution
- Enhanced Security: Protects sensitive data by ensuring only authorized individuals have access.
- Improved Compliance: Helps businesses adhere to regulatory requirements.
- Operational Efficiency: Reduces administrative workload by automating identity management tasks.
- Risk Mitigation: Identifies and addresses security gaps proactively.
Choosing the Right Identity Governance Solution
Organizations must consider several factors when selecting an identity governance solution:
- Scalability: The solution should support business growth and increased user base.
- Integration Capabilities: It should seamlessly integrate with existing IT infrastructure.
- User-Friendly Interface: An intuitive interface ensures ease of use for IT teams and business users.
- Cost-Effectiveness: Evaluate the pricing model to ensure it aligns with your organization’s budget.
- Customization & Flexibility: Should allow configuration based on organizational needs.
Conclusion
In the modern digital ecosystem, User Access Reviews, User Access Management, and Identity Governance and Administration solutions play a crucial role in strengthening security, ensuring compliance, and enhancing operational efficiency. By implementing a comprehensive identity governance solution, organizations can proactively manage user identities, mitigate risks, and maintain a robust security posture.
For organizations looking to enhance their a




Comments